The module lifecycle stage: Preview
Available in: EE
Description
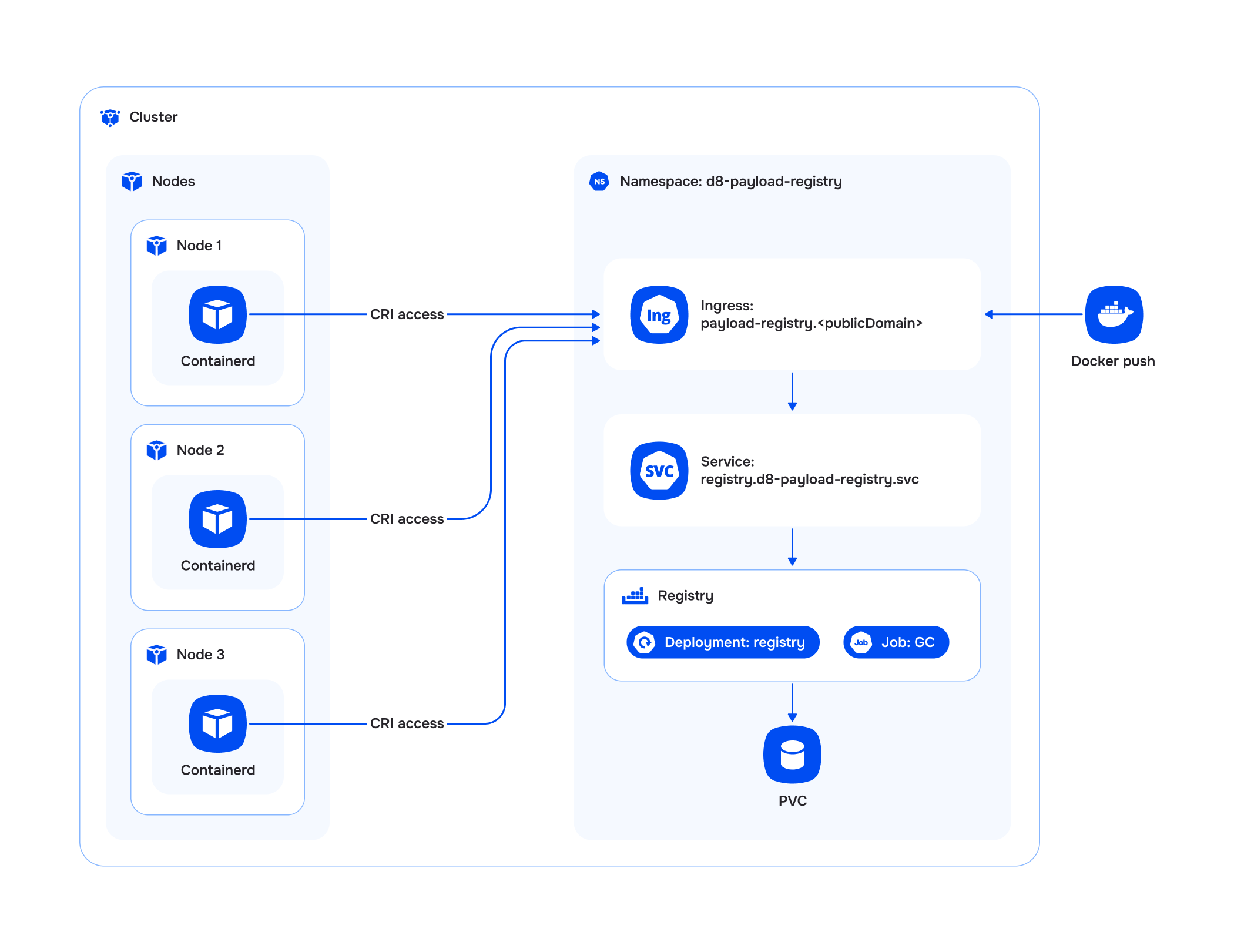
The payload-registry module implements a custom OCI container registry within the Deckhouse Kubernetes Platform.
Users and access
The module allows for the configuration of static authorization and project-based access management. Each project serves as a root directory in the registry and corresponds to the Kubernetes namespace name. There are two access levels: READ (allows pull operations) and FULL (allows both pull and push operations). If the specified namespace for the project does not exist, only READ access is granted.
User configuration is managed through ModuleConfig in the settings.users section. For more detailed usage examples, refer to the examples and FAQ sections.
Garbage Collection (GC)
The module supports the configuration of periodic garbage collection to clean up unused layers and untagged image manifests. The GC procedure is executed as a Kubernetes job and includes the following steps:
- Transition the registry to “read-only” mode.
- Execute the GC job to clean the registry.
- Return the registry to “read and write” mode.
GC settings are configured through ModuleConfig in the settings.gc section. For more detailed usage examples, refer to the examples and FAQ sections.
Limitations and Features
- The module is intended for storing payload images.
- Access to the registry is through Ingress at the address
payload-registry.${PUBLIC_DOMAIN}, wherePUBLIC_DOMAINis the value from thepublicDomainTemplateconfiguration in the globalModuleConfig.
Architecture