The module lifecycle stage: General Availability
Warning! Be sure that cert-manager issuer and module use same ingress class when you change module’s network configuration
Git SSH Operation on Port 22
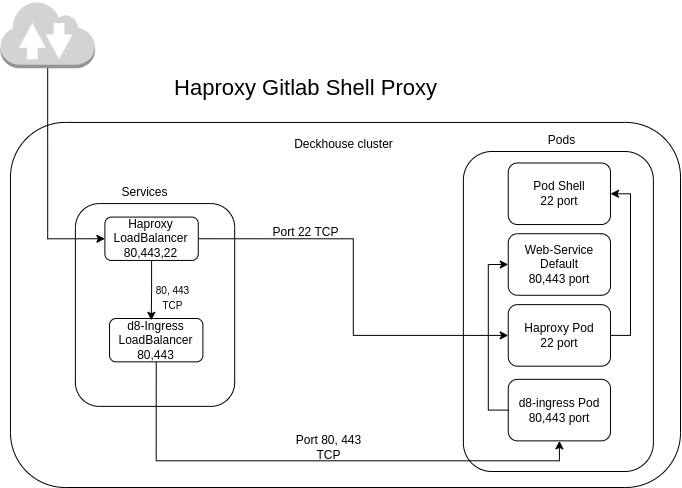
By default, the Deckhouse cluster uses the built-in Ingress controller — ingress-nginx. This controller provides access to the web interface (UI) via standard HTTP (port 80) and HTTPS (port 443) ports. However, ingress-nginx does not support TCP port proxying.
To proxy external TCP traffic through port 22 (Git SSH), a special option is provided in the module configuration. When this option is enabled, Haproxy is deployed with a service of type LoadBalancer. Haproxy forwards traffic from port 22 to the corresponding Git SSH Pod. Ports 80 and 443 continue to be handled by ingress-nginx, where TLS traffic termination occurs.
Self-signed certificates (certificates issued with internal Certificate Authority)
To use self-signed certificates in different connections (HTTPS, rediss, SMTPS etc…), create secret or configmap in d8-code namespace with certificates and declare it in CR:
...
spec:
network:
certificates:
customCAs:
- secret: custom-tls-ca
keys:
- ca.crt
- tls.crt
- secret: more-custom-CAs
keys:
- custom-ca-1.crt
- configMap: custom-CA-cm
- configMap: more-custom-CAs-cm
keys:
- custom-ca-2.crt
- custom-ca-3.crt
...
Features of the ownLoadBalancer option
Warning! ownLoadBalancer DOES NOT support the following modes:
HostPort,HostPortWithSSLPassthrough,HostPortWithProxyProtocol, andHostWithFailover.
-
Separate IP Address: When the
ownLoadBalancer.enabledoption is enabled for the Code module, a separate IP address is allocated, distinct from the main Deckhouse IP address. A separate DNS record must be created for this address. The following services will be accessible via this DNS record:- Web interface (UI) on ports 80 and 443.
- Git SSH on port 22.
-
Ignored Parameters: When the
ownLoadBalancer.enabledoption is enabled, the following parameters are ignored:spec.network.gitSsh.hostnamespec.network.gitSsh.service.typespec.network.gitSsh.service.nodePort
Instead, the
shellservice is assigned theLoadBalancertype, and Git SSH becomes accessible via the same domain as the web service.
Configuration Example
Below is an example of adding Haproxy for Git SSH proxying within ModuleConfig:
apiVersion: deckhouse.io/v1
kind: CodeInstance
metadata:
name: code
spec:
...
network:
ownLoadBalancer:
enabled: true
...
Haproxy Workflow Diagram
Haproxy inside the Deckhouse cluster operates according to the following diagram: