Available in editions: CE, BE, SE, SE+, EE
The module lifecycle stage: General Availability
The module has 1 alert.
The module is enabled by default in the Default bundle.
The module is disabled by default in the following bundles: Managed, Minimal.
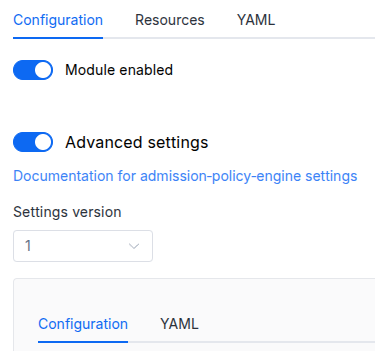
Parameters
Schema version: 1
- objectsettings
- array of stringssettings.clusterDomainAliases
A list of cluster domain aliases; these are resolved on par with
global.discovery.clusterDomain.Please note: the domain alias must not match the domain used in the DNS name template in the publicDomainTemplate parameter.
- stringElement of the array
Pattern:
^[0-9a-zA-Z\.-]+$
- booleansettings.enableLogs
Enable CoreDNS logging.
Default:
false - array of objectssettings.hosts
Not required value.
A static list of hosts similar to that of
/etc/hosts.- stringsettings.hosts.domain
Pattern:
^[0-9a-zA-Z\.-]+$ - stringsettings.hosts.ip
Pattern:
^[0-9]{1,}\.[0-9]{1,}\.[0-9]{1,}\.[0-9]{1,}$
- array of objectssettings.stubZones
A list of additional zones CoreDNS should be authoritative for.
Default:
[]Example:
stubZones: - zone: example.com upstreamNameservers: - 8.8.8.8 cacheTTLSeconds: 3600 transportProtocolMode: PreferUDP- integersettings.stubZones.cacheTTLSeconds
Max TTL in seconds for NOERROR responses.
Default:
30Allowed values:
1 <= X <= 3600 - stringsettings.stubZones.transportProtocolMode
The mode of the transport protocol for communicating with the upstream DNS server:
PreferUDP— UDP is used, even if the original request came over TCP. Note that if the DNS response from the upstream DNS server exceeds 512 bytes and has been truncated and marked with the TC bit (RFC 1035), then it will be resent over TCP (RFC 5966). The request will not be resent over TCP if there are other UDP issues.ForceTCP— Always uses TCP, even if the original request is over UDP.KeepOriginal— Uses the same protocol (TCP or UDP) as the original request.
Default:
PreferUDPAllowed values:
PreferUDP,ForceTCP,KeepOriginal - array of stringssettings.stubZones.upstreamNameservers
Required value
A list of IP addresses of recursive DNS servers that CoreDNS will use to resolve domains in this zone.
- stringElement of the array
Pattern:
^[0-9]{1,}\.[0-9]{1,}\.[0-9]{1,}\.[0-9]{1,}(:[0-9]{1,})?$
- stringsettings.stubZones.zone
Required value
The CoreDNS zone.
Pattern:
^[0-9a-zA-Z\.\-_]+$Example:
zone: consul.local
- stringsettings.transportProtocolMode
The mode of the transport protocol for communicating with the upstream DNS server:
PreferUDP— UDP is used, even if the original request came over TCP. Note that if the DNS response from the upstream DNS server exceeds 512 bytes and has been truncated and marked with the TC bit (RFC 1035), then it will be resent over TCP (RFC 5966). The request will not be resent over TCP if there are other UDP issues.ForceTCP— Always uses TCP, even if the original request is over UDP.KeepOriginal— Uses the same protocol (TCP or UDP) as the original request.
Default:
PreferUDPAllowed values:
PreferUDP,ForceTCP,KeepOriginal - array of stringssettings.upstreamNameservers
A list of IP addresses of recursive DNS servers that CoreDNS will use to resolve external domains.
By default, the
/etc/resolv.conflist is used.- stringElement of the array
Pattern:
^[0-9]{1,}\.[0-9]{1,}\.[0-9]{1,}\.[0-9]{1,}(:[0-9]{1,})?$