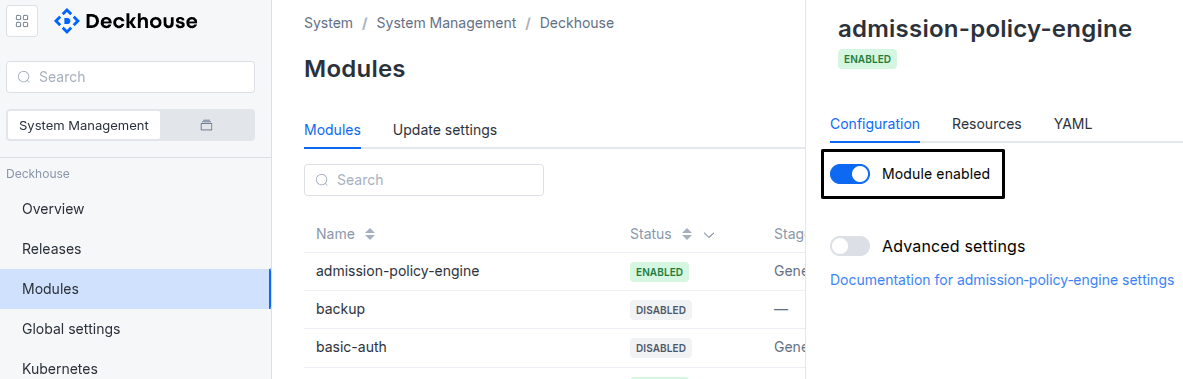
Available in editions: CE, BE, SE, SE+, EE
The module lifecycle stage: General Availability
The module has 46 alerts.
The module is enabled by default in the following bundles: Default, Managed.
The module is disabled by default in the Minimal bundle.
Requirements
To the versions of other modules:
-
prometheus: any version.
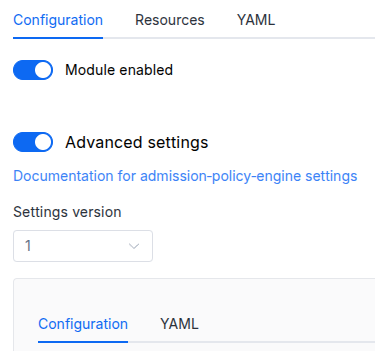
Parameters
Schema version: 1
- objectsettings
- booleansettings.ebpfExporterEnabled
Set to ‘false’ to disable ebpf_exporter in case it behaves incorrectly.
Default:
trueExample:
ebpfExporterEnabled: false - booleansettings.highAvailability
Manually enable the high availability mode.
By default, Deckhouse automatically decides whether to enable the HA mode. Click here to learn more about the HA mode for modules.
Examples:
highAvailability: truehighAvailability: false - objectsettings.nodeSelector
The same as in the pods’
spec.nodeSelectorparameter in Kubernetes.If the parameter is omitted or
false, it will be determined automatically.Example:
nodeSelector: disktype: ssd - array of objectssettings.tolerations
The same as in the pods’
spec.tolerationsparameter in Kubernetes;If the parameter is omitted or
false, it will be determined automatically.Example:
tolerations: - key: key1 operator: Equal value: value1 effect: NoSchedule- stringsettings.tolerations.effect
- stringsettings.tolerations.key
- stringsettings.tolerations.operator
- integersettings.tolerations.tolerationSeconds
- stringsettings.tolerations.value
- objectsettings.vpa
VPA settings for
kube-state-metricspods.Example:
vpa: kubeStateMetricsMaxCPU: 130m kubeStateMetricsMaxMemory: 115Mi- settings.vpa.kubeStateMetricsMaxCPU
The maximum value that the VPA can set for the CPU requests.
Examples:
kubeStateMetricsMaxCPU: 3kubeStateMetricsMaxCPU: 1000m - settings.vpa.kubeStateMetricsMaxMemory
The maximum memory requests the VPA can set.
Example:
kubeStateMetricsMaxMemory: 3Mi